Kerberos Is Best Described as a Protocol for
The basic protocol The Kerberos authentication protocol is the default authentication protocol of Windows Server 2003. A Kerberos ticket provides secure transport of a session key.

Common Tcp Ip Ports And Protocols Professional Computer Etsy Technology Posters Office Artwork Professional Art
Kerberos provides a means of verifying the identities of principals on an open unprotected network.

. For convincing 2 parties of each others identity and for exchanging session keys. Intraditional systems the users identity is verified by checking apassword typed during login. Cryptography - Authentication Protocols Kerberos.
Developed at MIT in the 1980s it became an IETF Standard in 1993. Kerberos is available in many commercial products as well. Kerberos is a network authentication protocol and designed to provide strong authentication and improved security for users and clientserver applications.
Strong and Diverse Security Measures. Active Directory and other Identity management like freeipa use it for offer a single sign-on authentication method. Passwords do not get sent over networks and all secret keys are encrypted.
The system records the identity and usesit to determine what. In order to break down the complexity of the protocol we will approach it in five steps. Give an answer to this need is the scope of this article.
What is Kerberos Used For. Kerberos a network authentication protocol included in the Microsoft Windows operating systems can now be used in conjunction with Security Support Provider Interface SSPI to provide pass-through authentication with secret key cryptography and data integrity. Passwords are never sent over the network unencrypted.
Kerberos is the most commonly usedexample of this type of authentication technology. Various operating systems support it. Kerberos is the protocol most used in modern authentication system.
Kerberos is a computer network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to. Industrial society requires a willing workforce c. Describes the best practices location.
Innovation is rewarded d. The Kerberos KDC distributes the session key by sending it. Kerberos is a network authentication protocol.
This section examines how the. Of course a good kerberos understanding is necessary by system administrator. It is the task of each specific implementation to support and best negotiate the various types of encryption.
People whose beliefs clash with those of industrial society are labeled deviants b. Although Kerberos is ubiquitous in the digital world it is widely used in secure systems based on reliable testing and verification features. Kerberos is one of the oldest authentication protocols in existence and it has been heavily used by Microsoft for authentication purposes for decades.
The operation of the protocol is based on the Needham-Schroeder protocol which defines a. It is also ideal for securing multi-tier application architectures especially when components of the application reside on different operating systems. Kerberos is a security protocol in Windows introduced in Windows 2000 to replace the antiquated NTLM used in previous versions of Windows.
A free implementation of this protocol is available from the Massachusetts Institute of Technology. Apart from direct use in signing messages. Tickets in Kerberos have a limited period.
Kerberos ˈ k ɛər b ər ə s is a computer network authentication protocol which works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Kerberos authentication is based on symmetric key cryptography. The Kerberos version 5 authentication protocol provides the default mechanism for authentication services and the authorization data necessary for a user to access a resource and perform a task on that resource.
Although Kerberos can be found everywhere in the digital world it is commonly used in secure systems that rely on robust authentication and auditing capabilities. Have discussed hash algorithms and digital signatures in abstract. Kerberos security authentication protocols employ cryptography multiple secret keys and third-party authorization creating a strong secure defense.
Kerberos 1 is an authentication service developed at MIT Massachusetts Institute of Technologythat uses symmetric key encryption techniques and a key distribution centre. Modern computer systems provide service to multiple users and requirethe ability to accurately identify the user making a request. The weakness of this encryption plus other protocol vulnerabilities have made Kerberos 4 obsolete.
Kerberos is used for Posix Active Directory NFS and Samba authentication. When using Kerberos the client does not need to handle the password and it is not sent over the network. Kerberos has several important advantages.
Another key use is in mutual authentication. Version 5 of Kerberos however does not predetermine the number or type of encryption methodologies supported. It is also an alternative authentication system to SSH POP and SMTP.
The Kerberos KDC provides scalability. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Kerberos is a Network Authentication Protocol evolved at MIT which uses an encryption technique called symmetric key encryption and a key distribution center.
It is an add-system that can be used with existing network. In Kerberos Clients and services are mutually authenticated. Describes the Kerberos Policy settings and provides links to policy setting descriptions.
People who fail to show respect for authority are likely to be considered deviant. Limitations of Kerberos Of the three As Kerberos only provides authentication Other protocols such as NIS or LDAP are still needed for authorization Applications must be Kerberized to take advantage Kerberos provides standard APIs to help with this There are also PAM modules for Kerberos authentication Cannot migrate existing password hashes into the. The authentication protocol Kerberos allows a number of computers to prove their identity among them safely over an insecure network.
Kerberos is used in Posix authentication. If the ticket gets stolen it is hard to reuse the ticket because of strong authentication needs.

Dp Computer Kerberos 25 Apr 17 Subscribe Us Www Youtube Com C Mahendraguruvideos Join Us Facebook Ww Cryptography Study Materials Networking

Kerberos Solution Diagram Infographic Picture Explained

Kerberos Protocol Software Development Development Math
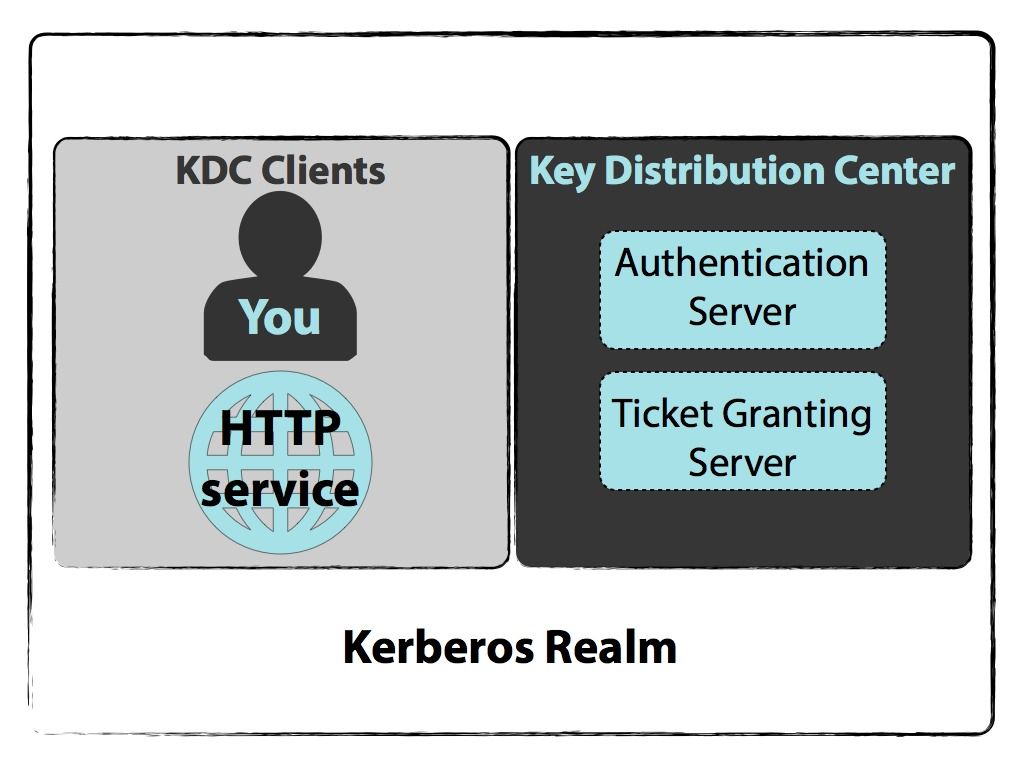
Explain Like I M 5 Kerberos Lynn Root Explained Cryptography Learning
Comments
Post a Comment